How Secure Are Locked Smartphones?
Locked smartphones can be both a treasure trove of information and a formidable barrier. Whether it’s an iPhone or Android, a locked device is more than a mere inconvenience; it’s a barrier to valuable data that could be crucial for personal or legal reasons. At Artemis Forensics, we specialize in unlocking this barrier, ensuring that your vital information remains accessible and secure.
First we need to understand the states of locked devices, specifically AFU (After First Unlock) and BFU (Before First Unlock). These states play an important role in determining the accessibility and security of data on locked iPhone and Android devices.
The States of Locked Devices: AFU vs. BFU
1. After First Unlock (AFU)


Definition: AFU refers to a state where a device has been unlocked at least once after a reboot.
Data Accessibility: In AFU mode, the encryption keys for accessing most of the data on the device are in memory. Using specialized forensic tools this can make it easier to extract a wide range of data for forensic purposes, including app data, messages, and more.
Indicators
• Notifications may display content on the lock screen.
• Biometric authentication (like fingerprint or facial recognition) is usually available to unlock the device.
• Camera application is usually accessible from the lock screen.
2. Before First Unlock (BFU)
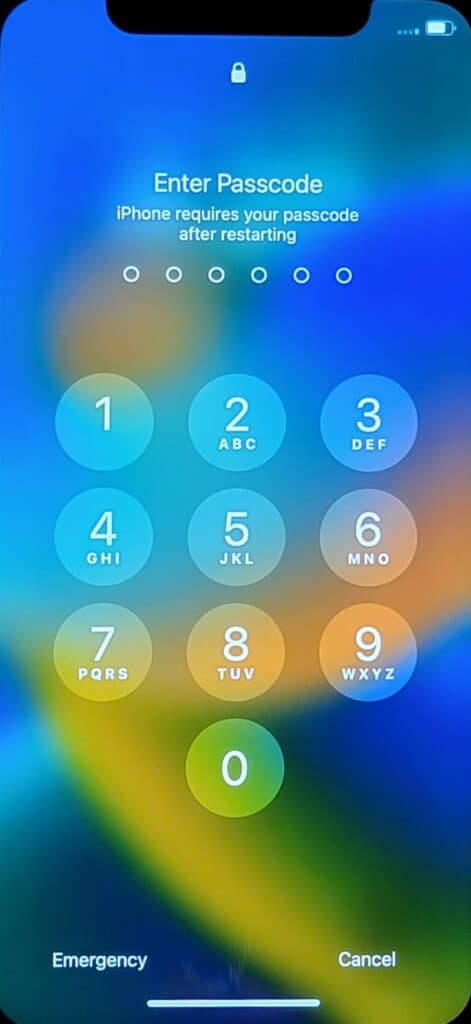
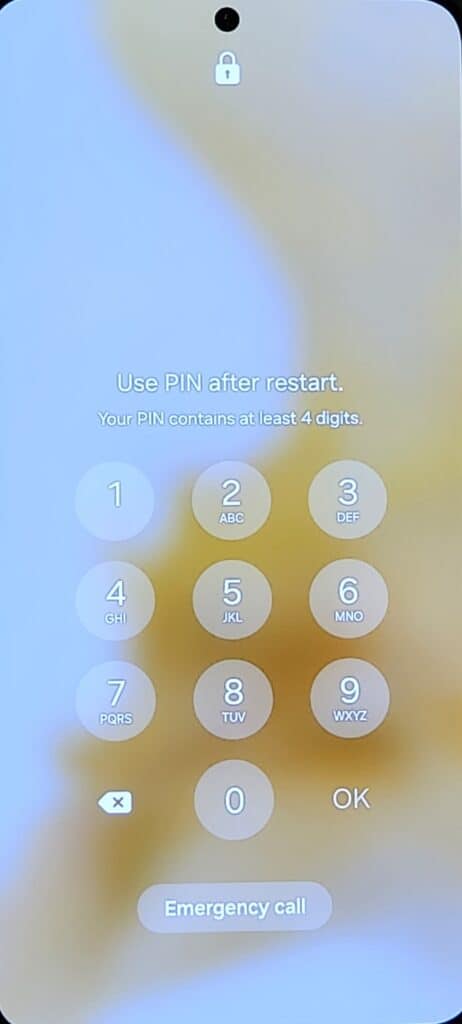
Definition: BFU is the state of a device that has not been unlocked since its last reboot. In this state, the encryption keys are not loaded into the memory.
Data Accessibility: Retrieving data from a device in BFU mode is significantly more challenging. Most personal and application data remain securely encrypted and are inaccessible without the correct passcode. Biometrics (such as fingerprint or face scans) cannot be used to unlock the device. A passcode is required to transition the device from BFU to AFU.
Indicators
- iPhones will typically show a message like “iPhone requires your passcode after restarting”.
- Androids will show a message like “Use PIN after restart”.
- Camera is not accessible.
- Notifications and notifications content may not be displayed on the screen.
- Biometric authentication options are not available.
Impact on Forensic Data Extraction
The state of a device (AFU or BFU) greatly influences the approach and success rate of forensic investigations. In AFU, forensic experts have a higher chance of retrieving data without the need for the passcode. In BFU, the extraction process is more complex, and the likelihood of a successful data extraction is lowered. In some cases, brute force attempts to recover the passcode of a device in BFU state can take decades.
It’s important to understand these states, especially when preparing to ship devices for forensic analysis. Preserving the AFU state (by not rebooting the device or allowing it to run out of power) can be advantageous for data recovery.
Understanding the differences between AFU and BFU is not just a technical necessity; it’s a step towards informed decision-making when dealing with locked devices. Whether you’re a law enforcement officer, legal professional, a business owner, or an individual facing a locked device scenario, this knowledge is essential for successful data recovery and security.
Preserving Data on Locked Devices
When dealing with locked smartphones, preserving existing data is paramount, especially in scenarios where forensic analysis may be required. Here’s how to ensure data integrity on locked iPhones and Android devices:
- Never attempt a factory reset on a locked device. This can lead to permanent data loss, as it erases all user data and settings.
- Keep the device charged. A dead battery can result in a device reboot, which may shift it from AFU (After First Unlock) to BFU (Before First Unlock) state, complicating data extraction.

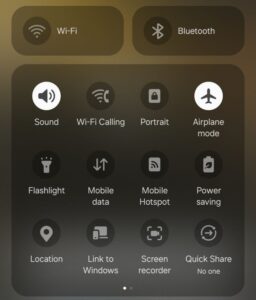
- If possible, turn on airplane mode. Make sure that Wi-Fi, mobile data, Bluetooth, location, and other wireless connections are turned off. Note that depending on user settings, you may not have access to these options on a locked device.
- Do not attempt to guess the passcode excessively, as this could trigger additional security measures, such as a device wipe after a certain number of incorrect attempts.
- Avoid using unverified software or DIY methods to unlock your device. Such attempts can lead to data loss.
- If you have any known passwords, passcodes, or pattern locks, securely provide this information to your forensic examiner. This aids in quicker access and data recovery.
When shipping locked devices:
- Ensure the device is fully charged before shipping. A device that powers down due to low battery could revert to a BFU state.
- Use a power bank to further increase battery life.

- Store the device in a Faraday bag. This is a special type of bag that blocks electromagnetic fields and signals, essentially isolating your device from external communications. This prevents potential remote lock or erase commands that can be initiated accidentally or by someone else. Alternatively, you can wrap the device in aluminum foil.

- Use bubble wrap or similar protective material to pack your device. This prevents physical damage during transit, which could pose additional risks to data integrity.
- Include the signed chain of custody form.

- Opt for a shipping service with tracking capabilities.
Legal And Compliance
The foremost consideration in accessing a locked device for forensic purposes is obtaining the necessary legal authorization. This may involve acquiring consent from the device owner or securing a warrant or court order, especially in criminal investigations. Unauthorized access, even for seemingly valid reasons, can lead to legal violations and potentially render any extracted data inadmissible in court.
Additionally, different jurisdictions may have varying laws regarding digital privacy and data access. What is permissible in one country or state may not be in another.
Final Thoughts
The delicate balance between accessibility and security is paramount when it comes to locked devices. Remember that your proactive measures can significantly impact the success of data recovery processes. For further assistance with data recovery from locked devices, contact us. We are committed to delivering professional and secure solutions.

