Ever Hit a Wall Recovering Deleted Data from SQLite Databases? Could the ‘Key’ to Finding a Lead Actually Lie in the Gaps?
Analyzing primary keys in SQLite databases offers invaluable insights into data integrity and potential deletions. A seamless sequence of primary keys indicates intact data, while gaps suggest deletions. By systematically examining adjacent keys, we can identify these gaps and reveal potential data removals.
Understanding Primary Keys
Before we dive deeper, let’s quickly clarify what a primary key is. In databases, a primary key is a unique identifier for each record in a table. Think of it as a special label on every piece of data, ensuring that no two pieces are exactly the same. When we talk about examining primary keys, we are essentially looking at these unique labels to understand the story they tell about our data, especially when some pieces of the story seem to be missing.
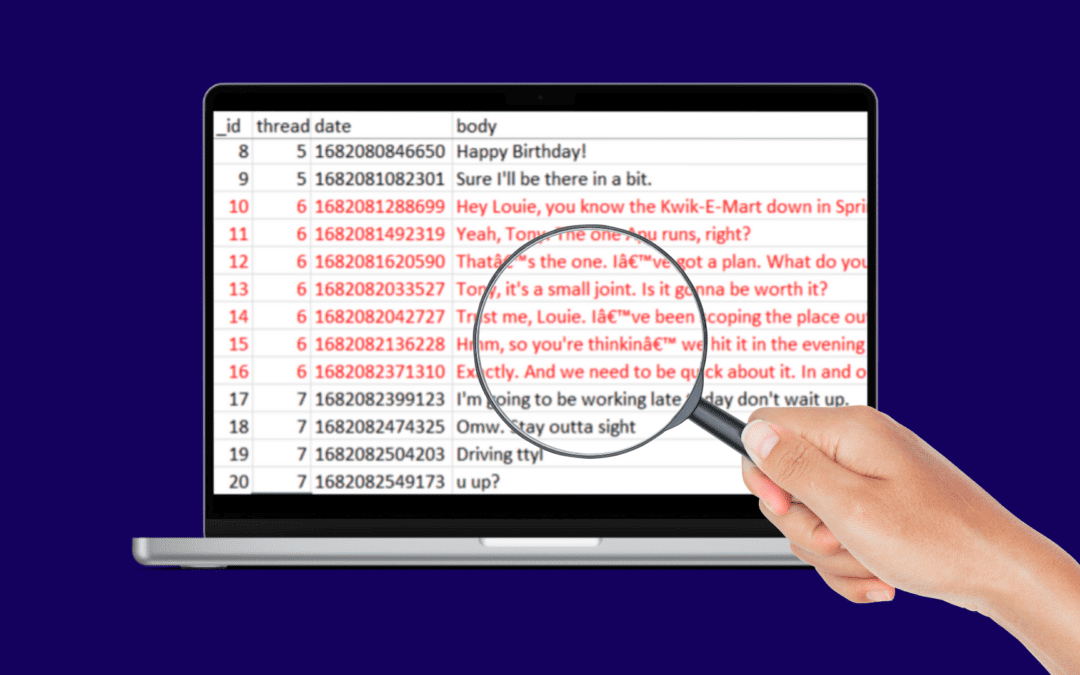
Imagine a scenario: a robbery suspect claims innocence and says he was sleeping during the time of the robbery, but his phone indicates texting application use during that time. While no messages from the robbery timeframe are visible and direct recovery of deleted texts is unsuccessful, gaps in the primary keys of the message database hint at deleted entries. These gaps, aligned with the timestamps, reveal a potential evidence trail, implying messages sent or received during the crime were deleted, thereby casting doubt on the suspect’s authenticity and providing investigators with a valuable lead when direct recovery methods fall short.
We’ll go over how you can review these gaps in the data and their value.
1. Open the Database:
Start by opening DB Browser and loading your SQLite database. For this example, we’re using the “mmssms.db” which stores text messages data on Android devices.
You can download DB Browser from:
Downloads – DB Browser for SQLite (sqlitebrowser.org)
2. Find the Table
Locate and select the table you want to examine. For this scenario, we’ll choose the “sms” table.
3. Identify the Primary Key Column:
Spot the primary key column that is needed for spotting data deletions. Under the “Database Structure” tab expand the table of interest and you’ll usually have a column with a key:
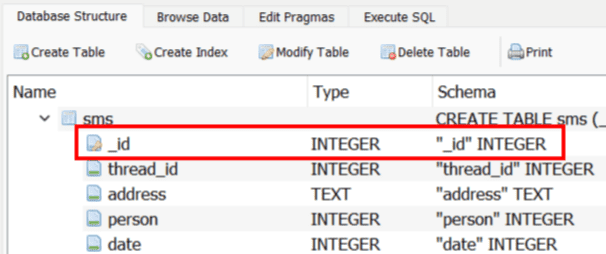
Here, we’ll focus on the “_id” column. If you go to the “Browse Data” tab and browse the “sms” table you can see the PKs.

4. Identify Gaps Using SQL Query
Utilize the “Execute SQL” tab to run SQL commands and identify gaps in primary key sequences with a query like the following:
SELECT a._id AS start_gap, MIN(b._id) AS end_gap
FROM sms a, sms b
WHERE a._id < b._id
GROUP BY a._id
HAVING MIN(b._id) > a._id + 1;
Observe the output to identify and analyze the gaps in primary keys.

The above screenshot shows 3 instances of gaps found within the “sms” table, indicating that these gaps in messaging are missing from the database and were likely deleted.
5. Analyzing Timeframes of Deletions:
After identifying gaps in the primary key sequence, incorporating timestamps in a human-readable format can further refine our analysis by providing more context for the identified data deletions.
The following SQL query selects IDs and their associated timestamps (date column), converting the Unix timestamps (note: your database may use different encoding) to a readable format.
SELECT a._id AS start_id,
datetime(a.date / 1000, ‘unixepoch’) AS start_date,
MIN(b._id) AS end_id,
datetime(MIN(b.date) / 1000, ‘unixepoch’) AS end_date
FROM sms a, sms b
WHERE a._id < b._id
GROUP BY a._id, a.date
HAVING MIN(b._id) > a._id + 1;

Reviewing the human-readable dates adjacent to the identified gaps gives insight into the timeframe of the now-missing data. It’s not an exact timestamp of when the deletion happened, but it provides a window into when the deleted data was created or last modified. Cross-reference these periods with other logs including application usage, network usage, location data, etc. to uncover related activities or incidents around the deletions.
6. Potential Caveats
While inspecting primary keys can hint at data deletions, it’s not foolproof. Actions like database cleaning, vacuuming, reindexing, deletion of all records, can eliminate primary key gaps.
Additionally, be cautious when correlating primary keys with timestamps, as anomalies can occur. Network issues, device settings, or syncing across multiple devices can result in discrepancies.
Nonetheless, when used in tandem with other device logs, analyzing primary keys can contribute to painting a more comprehensive and accurate picture of the user activity.
7. Automate Your Analysis with SQLite Primary Key Gap Analyzer
To streamline the process of identifying primary key gaps in SQLite databases, check out the SQLite Primary Key Gap Analyzer. This intuitive tool automates the analysis, saving you time and ensuring accuracy.
Get downloads and more information here!
8. Conclusion
Exploring the silent gaps left by deleted data, like our suspect’s messages during the robbery, can help your investigations. Through careful analysis of primary keys and timestamps in databases, you can spotlight these quiet hints, weaving together a story the deletions try to erase, and uncovering crucial leads in the investigation.